TL;DR: I created a new extension called Enforce Encryption. See extension description for a simple explanation of how it works and why using encrypted connections is important.
I realized that Stack Overflow is one of the few websites that I use with authentication and yet over plain unencrypted HTTP connections. So, what if I just change http:// into https:// in the address bar? Surprisingly, this worked, even though Stack Overflow doesn’t support HTTPS officially (way too many links lead back to HTTP).
So, if I want to use Stack Overflow over HTTPS now, how do I do it? All my history items lead to unencrypted pages. But even if I clean out my history, I regularly get to Stack Overflow pages via search or links. Switching to HTTPS manually every time is just unrealistic. That’s something where HTTP Strict Transport Security could help, if it were active for that site all links and history entries would be changed into HTTPS automatically.
Now Strict Transport Security is something that the website itself needs to enable. I briefly considered manipulating a response from Stack Overflow to include the necessary header. However, a search on MXR revealed that nsISiteSecurityService is responsible for handling Strict Transport Security in Firefox (starting with Firefox 26, before that the service was going under a different name). Now all I had to do was running a fairly simple line of JavaScript code from the Error Console and Strict Transport Security was enabled for Stack Overflow.
Only problem now: that approach doesn’t scale. There are other websites that should be using Strict Transport Security, e.g. google.com. If you simply type it into your address bar then the first request will go over plain HTTP and redirect to HTTPS then — this initial unencrypted request enables attacks like SSL stripping. A simpler way to check whether Strict Transport Security is enabled and enabling it if necessary would be nice.
HTTPS Everywhere extension sounds like it would work by utilizing Strict Transport Security but apparently it doesn’t. There is another extension called Force-TLS which actually allows managing all aspects of Strict Transport Security but it does that via its own preferences dialog in the charming style of Mozilla Suite’s Cookie Manager from year 2004. Better UI concepts have been developed since then and this setting is something I would expect in the Page Info dialog.
So I simply wrote my own extension called Enforce Encryption (not reviewed by Mozilla yet, that should take a few weeks). It is very minimalistic, in the current version it is merely a hundred lines of code. All it does is adding a checkbox to the Security tab of the Page Info dialog to enable or disable Strict Transport Security. It isn’t quite as flexible as Force-TLS, yet it should cover most use cases and be much easier to use. Enjoy!
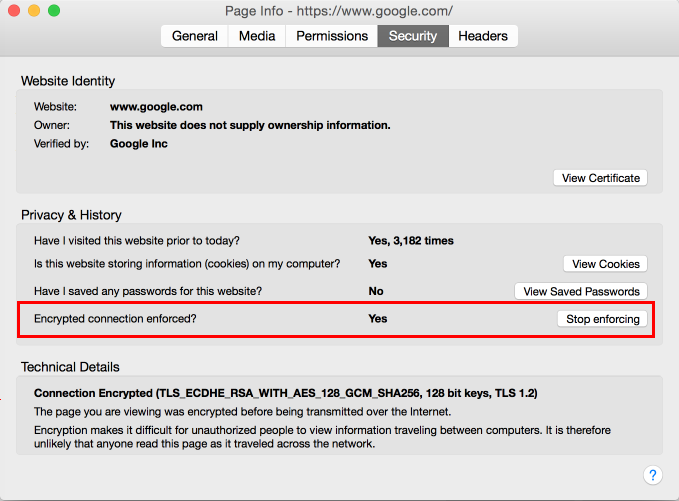
For reference, the source code is available on GitHub.
Comments
What is the exact difference between Enforce Encryption and HTTPS Everywhere?
HTTPS Everywhere is a very complex extension. It has a rules file that is larger than 1 MB in size, apparently it lists every website on the web known to have working HTTPS support. If you want to add one more site you need to learn how to write their rules (recommendation from HTTPS Everywhere FAQ). It will listen to all your connections and not only rewrite them to use HTTPS but also change cookies to ensure these are never sent over unencrypted connections. It has the SSL Observatory feature which is nice for people who know what it is about but scary for everybody else (meaning the majority of them).
Enforce Encryption on the other hand is simply about giving you a tool to enforce HTTPS connections on the websites you are using – and it doesn’t even implement this feature, it rather activates a built-in Firefox feature for you. You decide where and how you want to use it, there is no predefined list. The extension is tiny and very lightweight, the configuration interface minimal and unobtrusive.
Which one you should use depends on your requirements of course.
Not sure how relevant it is any more, as its about a year old, but this blog makes for interesting reading as to why Stack Overflow isn’t / wasn’t using SSL: http://nickcraver.com/blog/2013/04/23/stackoverflow-com-the-road-to-ssl/
Most of that blog post seems to be outdated by now. The SSL support on Stack Overflow is still incomplete but the main issue now is links and images using HTTP protocol – that’s something Strict Transport Security can take care of.