In September last year, a breach at LastPass’ parent company GoTo (formerly LogMeIn) culminated in attackers siphoning out all data from their servers. The criticism from the security community has been massive. This was not so much because of the breach itself, such things happen, but because of the many obvious ways in which LastPass made matters worse: taking months to notify users, failing to provide useful mitigation instructions, downplaying the severity of the attack, ignoring technical issues which have been publicized years ago and made the attackers’ job much easier. The list goes on.
Now this has been almost a year ago. LastPass promised to improve, both as far as their communication goes and on the technical side of things. So let’s take a look at whether they managed to deliver.
TL;DR: They didn’t. So far I failed to find evidence of any improvements whatsoever.
Update (2023-09-26): It looks like at least the issues listed under “Secure settings” are finally going to be addressed.

Contents
The communication
The initial advisory
LastPass’ initial communication around the breach has been nothing short of a disaster. It happened more than three months after the users’ data was extracted from LastPass servers. Yet rather than taking responsibility and helping affected users, their PR statement was designed to downplay and to shift blame. For example, it talked a lot about LastPass’ secure default settings but failed to mention that LastPass never really enforced those. In fact, people who created their accounts a while ago and used very outdated (insecure) settings never saw as much as a warning.
The statement concluded with “There are no recommended actions that you need to take at this time.” I called this phrase “gross negligence” back when I initially wrote about it, and I still stand by this assessment.
The detailed advisory
It took LastPass another two months of strict radio silence to publish a more detailed advisory. That’s where we finally learned some more about the breach. We also learned that business customers using Federated Login are very much affected by the breach, the previous advisory explicitly denied that.
But even now, we learn that indirectly, in recommendation 9 out of 10 for LastPass’ business customers. It seems that LastPass considered generic stuff like advice on protecting against phishing attacks more important than mitigation of their breach. And then the recommendation didn’t actually say “You are in danger. Rotate K2 ASAP.” Instead, it said “If, based on your security posture or risk tolerance, you decide to rotate the K1 and K2 split knowledge components…” That’s the conclusion of a large pile of text essentially claiming that there is no risk.
At least the advisory for individual users got the priorities right. It was master password first, iterations count after that, and all the generic advice at the end.
Except: they still failed to admit the scope of the breach. The advice was:
Depending on the length and complexity of your master password and iteration count setting, you may want to reset your master password.
And this is just wrong. The breach already happened. Resetting the master password will help protect against future breaches, but it won’t help with the passwords already compromised. This advice should have really been:
Depending on the length and complexity of your master password and iteration count setting, you may want to reset all your passwords.
But this would amount to saying “we screwed up big time.” Which they definitely did. But they still wouldn’t admit it.
Improvements?
A blog post by the LastPass CEO Karin Toubba said:
I acknowledge our customers’ frustration with our inability to communicate more immediately, more clearly, and more comprehensively throughout this event. I accept the criticism and take full responsibility. We have learned a great deal and are committed to communicating more effectively going forward.
As I’ve outlined above, the detailed advisory published simultaneously with this blog post still left a lot to be desired. But this sounds like a commitment to improve. So maybe some better advice has been published in the six months which passed since then?
No, this doesn’t appear to be the case. Instead, the detailed advisory moved to the “Get Started – About LastPass” section of their support page. So it’s now considered generic advice for LastPass users. Any specific advice on mitigating the fallout of the breach, assuming that it isn’t too late already? There doesn’t seem to be any.
The LastPass blog has been publishing lots of articles again, often multiple per week. There doesn’t appear to be any useful information at all here however, only PR. To add insult to injury, LastPass published an article in July titled “How Zero Knowledge Keeps Passwords Safe.” It gives a generic overview of zero knowledge which largely doesn’t apply to LastPass. It concludes with:
For example, zero-knowledge means that no one has access to your master password for LastPass or the data stored in your LastPass vault, except you (not even LastPass).
This is bullshit. That’s not how LastPass has been designed, and I wrote about it five years ago. Other people did as well. LastPass didn’t care, otherwise this breach wouldn’t have been such a disaster.
Secure settings
The issue
LastPass likes to boast how their default settings are perfectly secure. But even assuming that this is true, what about the people who do not use their defaults? For example the people who created their LastPass account a long time ago, back when the defaults were different?
The iterations count is particularly important. Few people have heard about it, it being hidden under “Advanced Settings.” Yet when someone tries to decrypt your passwords, this value is an extremely important factor. A high value makes successful decryption much less likely.
As of 2023, the current default value is 600,000 iterations. Before the breach the default used to be 100,100 iterations, making decryption of passwords six times faster. And before 2018 it was 5,000 iterations. Before 2013 it was 500. And before 2012 the default was 1 iteration.
What happened to all the accounts which were created with the old defaults? It appears that for most of these LastPass failed to fix the settings automatically. People didn’t even receive a warning. So when the breach happened, quite a few users reported having their account configured with 1 iteration, massively weakening the protection provided by the encryption.
It’s the same with the master password. In 2018 LastPass introduced much stricter master password rules, requiring at least 12 characters. While I don’t consider length-based criteria very effective to guide users towards secure passwords, LastPass failed to enforce even this rule for existing accounts. Quite a few people first learned about the new password complexity requirement when reading about the breach.
Improvements?
I originally asked LastPass about enforcing a secure iterations count setting for existing accounts in February 2018. LastPass kept stalling until I published my research without making certain that all users are secure. And they ignored this issue another four years until the breach happened.
And while the breach prompted LastPass to increase the default iterations count, they appear to be still ignoring existing accounts. I just logged into my test account and checked the settings:
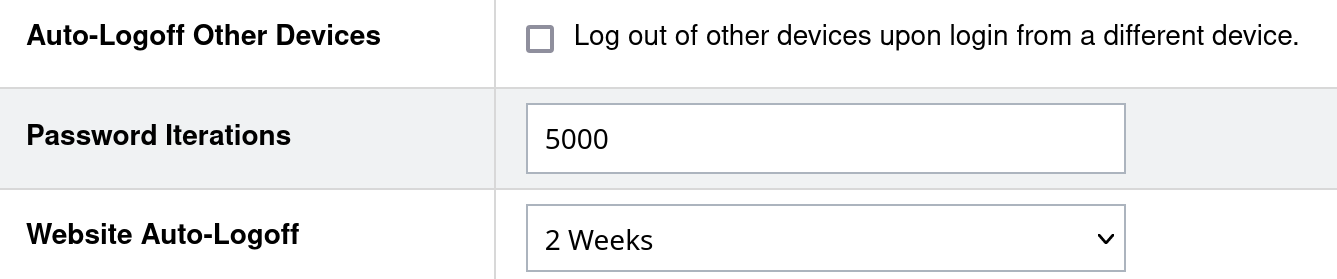
There is no warning whatsoever. Only if I try to change this setting, a message pops up:
For your security, your master password iteration value must meet the LastPass minimum requirement: 600000
But people who are unaware of this setting will not be warned. And while LastPass definitely could update this setting automatically when people log in, they still choose not to do it for some reason.
It’s the same with the master password. The password of my test account is weak because this account has been created years ago. If I try to change it, I will be forced to choose a password that is at least 12 characters long. But as long as I just keep using the same password, LastPass won’t force me to change it – even though it definitely could.
There isn’t even a definitive warning when I log in. There is only this notification in the menu:
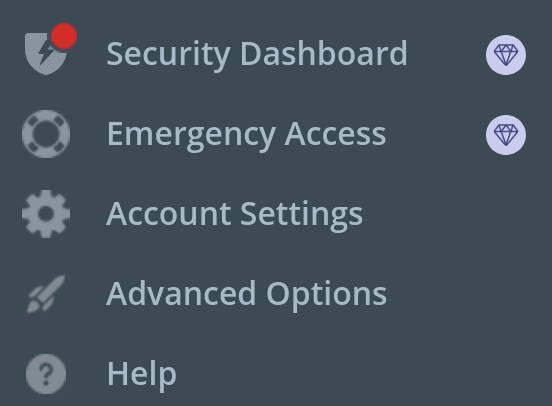
Only after clicking “Security Dashboard” will a warning message show up:
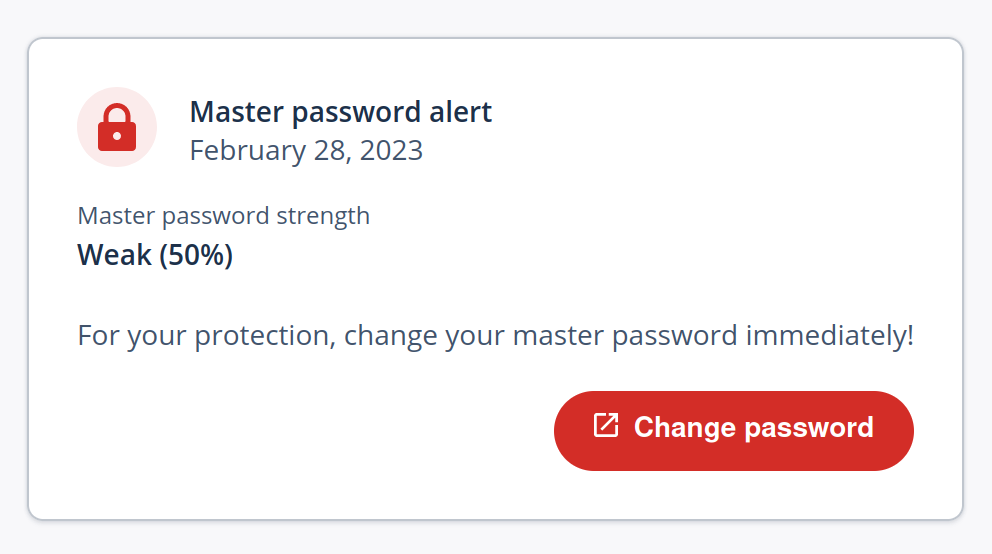
If this is such a critical issue that I need to change my master password immediately, why won’t LastPass just tell me to do it when I log in?
This alert message apparently pre-dates the breach, so there don’t seem to be any improvements in this area either.
Update (2023-09-26): Last week LastPass sent out an email to all users:
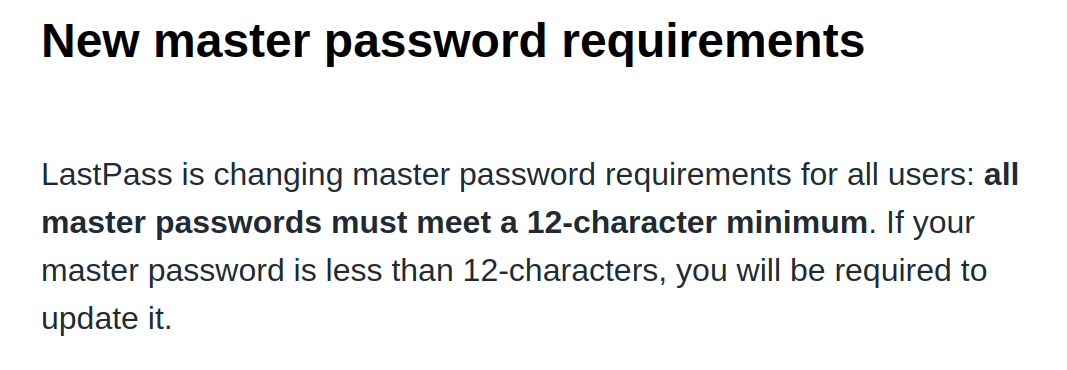
According to this email, LastPass will start enforcing stronger master passwords at some unspecified point in future. Currently, this requirement is still not being enforced, and the email does not list a timeline for this change.
More importantly, when I logged into my LastPass account after receiving this email, the iterations count finally got automatically updated to 600,000. The email does not mention any changes in this area, so it’s unclear whether this change is being applied to all LastPass accounts this time.
Brian Krebs is quoting LastPass CEO with the statement: “We have been able to determine that a small percentage of customers have items in their vaults that are corrupt and when we previously utilized automated scripts designed to re-encrypt vaults when the master password or iteration count is changed, they did not complete.” Quite frankly, I find this explanation rather doubtful.
First of all, reactions to my articles indicate that the percentage of old LastPass accounts which weren’t updated is far from small. There are lots of users finding an outdated iterations count configured in their accounts, yet only two reported their accounts being automatically updated so far.
Second: my test account in particular is unlikely to contain “corrupted items” which previously prevented the update. Back in 2018 I changed the iterations count to 100,000 and back to 5,000 manually. This worked correctly, so no corruption was present at that point. The account was virtually unused after that except for occasional logins, no data changes.
Unencrypted data
The issue
LastPass PR likes to use “secure vault” as a description of LastPass data storage. This implies that all data is secured (encrypted) and cannot be retrieved without the knowledge of the master password. But that’s not the case with LastPass.
LastPass encrypts passwords, user names and a few other pieces of data. Everything else is unencrypted, in particular website addresses and metadata. That’s a very bad idea, as security researchers kept pointing out again and again. In November 2015 (page 67). In January 2017. In July 2018. And there are probably more.
LastPass kept ignoring this issue. So when last year their data leaked, the attackers gained not only encrypted passwords but also plenty of plaintext data. Which LastPass was forced to admit but once again downplayed by claiming website addresses not to be sensitive data. And users were rightfully outraged.
Improvements?
Today I logged into my LastPass account and then opened https://lastpass.com/getaccts.php. This gives you the XML representation of your LastPass data as it is stored on the server. And I fail to see any improvements compared to this data one year ago. I gave LastPass the benefit of the doubt and created a new account record. Still:
<account url="68747470733a2f2f746573742e6465" last_modified="1693940903" …>
The data in the url field is merely hex-encoded which can be easily translated back into https://test.de. And the last_modified field is a Unix timestamp, no encryption here either.
Conclusions
A year after the breach, LastPass still hasn’t provided their customers with useful instructions on mitigating the breach, nor has it admitted the full scope of the breach. They also failed to address any of the long-standing issues that security researchers have been warning about for years. At the time of writing, owners of older LastPass accounts still have to become active on their own in order to fix outdated security settings. And much of LastPass data isn’t being encrypted.
I honestly cannot explain LastPass’ denial to fix security settings of existing accounts. Back when I was nagging them about it, they straight out lied to me. Don’t they have any senior engineers on staff, so that nobody can implement this change? Do they really not care as long as they can blame the users for not updating their settings? Beats me.
As to not encrypting all the data, I am starting to suspect that LastPass actually wants visibility into your data. Do they need to know which websites you have accounts on in order to guide some business decisions? Or are they making additional income by selling this data? I don’t know, but LastPass persistently ignoring this issue makes me suspicious.
Either way, it seems that LastPass considers the matter of their breach closed. They published their advisory in March this year, and that’s it. Supposedly, they improved the security of their infrastructure, which nobody can verify of course. There is nothing else coming, no more communication and no technical improvements. Now they will only be publishing more lies about “zero knowledge architecture.”
Comments
MFA seeds were also stolen in the breach. Notice was buried in one of the notices/support articles that they published. Of course the instructions to do so were in another article linked from that one.
If you didn't proactively reseed, they did it for you and it appears didn't communicate it well enough.
Thanks again for your fruitful insights into Lastpass. I was a customer and have moved to another password manager.
I am curious if their subscriber base has shrunk due to their ineptitude. After some googling, i couldn't uncover any concrete numbers.
It could also explain their non-movement on these critical items. If it was a minimal drop in revenue, then keep staying the course and do not change a thing.
I'm not a techie, but LastPass is charging me as a customer and telling me me data is secure when apparently it's not as secure as it should be. Maybe it's time to find a new password manager.
I've been. With LP for years but have switched password mgrs several months ago. It just became too buggy to be secure. I also liked that the CEO has accepted blame & responsibility. The CEO who is as inept as the service & will never take any responsibility nor pay the cost of creating this breach in the first place.
I’m not sure I understand your comment correctly, but the LastPass CEO didn’t actually accept the responsibility. He merely said that he did. But he didn’t even acknowledge what he did wrong, which would have been the prerequisite for outlining the consequences.
Rumours says the OP had to take care of lastpass server by himself after consecutive failed attempts of letting lastpass know their issues.
So if a news comes out regarding OP being involved, mention me there with credits
I think that the vault being an opaque blob brings one more risk (albeit probably smaller): unless pieces of data are encrypted with additional data that indicates what they are, an attacker who has compromised the vault storage can permute them around and e.g. cause a password to be used on a different site than it's actually for (e.g. on an attacker-controlled one).
I guess you meant to write “the vault not being an opaque blob”?
Yes, compromised server associating an existing password with a different website is a risk, one that I notified LastPass about in January 2018. My report was about EquivalentDomains not being encrypted, but attackers could really manipulate the URL field just as well. LastPass paid a bug bounty for the report and resolved it in August 2018 without actually fixing the issue. The replies on similar submissions went into the direction that a compromised server is not considered an issue because the server is well-protected.
LastPass is dead after they sold the company. Don't know why we keep hoping they will change anything. It's pretty obvious they don't care and most of the original people who have brains have left. This is just a company now to earn money before the next breach. Once that happens they will pay a fine. The company I worked for offered LastPass but it took the 2 breach to move on. Luckily I had moved on way past the first breach.
Quite frankly, I’m not sure why people see LastPass being sold as a relevant event in the product’s history. LastPass had their first two breaches before they’ve been acquired, and the response to those was already very underwhelming. Their bad crypto also pre-dates the acquisition.
This article could have been do much shorter. "If you haven't canceled your LastPass account, what are you waiting for? Really!" Anything longer than that was simply verbose.
Be good if the author could have recommended a new password manager?
Also, is there a pain free way to change ones passwords as in 100s of them?
Sorry, I am not the right person to recommend password managers – I’m typically looking at issues, not at advantages.
I also don’t know a good way of changing many passwords, other than prioritizing the important ones (everything that’s somehow tied to money or your identity).
What I don't understand (or completely overlooked in the news) is why nobody sued LastPass. I mean companies and people are sued for much less then this in the US. It can't be that nobody has actual damage because of all their passwords leaked, or did the hackers just hack LastPass and then deleted their looted data, not selling or using it anyway or anywhere?
They have been sued all right. See https://www.pcmag.com/news/lastpass-faces-class-action-lawsuit-over-password-vault-breach for example. There should still be more of this of course, but the trouble seems to be indeed proving damage caused.
Still haven't read the full article, but please correct the repeated use of "advise" for "advice". Two different things, one a verb and the other a noun. You want the noun.
Wow just wanted to say thanks for a clear breakdown on what's going on with LastPass. I was linked this article and have since gone through some of your other excellent posts.
LastPass was the first password manager I heard about many years ago. When the idea of a password manager came up I initially looked at LP but ended up going with a different manager due to the unpleasing UI. I'm glad I did!
I just found that LastPass now offers a way of rotating K1 and K2 for SSO accounts without defederating them. I have not completed/tested this process, but wanted to relay the info. https://support.lastpass.com/s/document-item?language=en_US&bundleId=lastpass&topicId=LastPass/rotate_knowledge_components_for_azure_ad.html&_LANG=enus
I’m mostly certain that this document isn’t what you think it is. Azure Active Directory is also providing Federated Login, and it is also based on K1 and K2 components. And Microsoft also suffered a breach recently that compromised their data. It’s quite ironic that LastPass is being more proactive about Microsoft’s breach than about their own.
I work for a company that gives a LastPass account to every employee. Fortunately I and many of my colleagues didn't use it. But the company didn't say a word about the LastPass breach -- no 'update your password' or 'change vault passwords,' nada. And the LastPass wasn't integrated into SSO or anything. I couldn't believe it. I imagine there are a lot of corporations similar to mine with plenty of sitting duck users.
The last few weeks, multiple accounts of mine have been compromised. I was a customer of Lastpass up until the leak last year.
Now I can't guarantee that someone decrypted the passwords or that my accounts being compromised is in any way connected.
But I am lazy and didn't change all my passwords.
I was wondering if anybody else got compromised in the last weeks.